Structure + Content
Organizations today are increasingly turning to Linux as a platform of choice for many organizations, product manufacturers, and service providers.
Portrait
Linux is being used for large supercomputers and clusters, for cloud and virtualization infrastructure, and for backend storage and database servers. Linux is used for Internet facing services, firewalls, and edge computing. In addition to scalable enterprise infrastructure, Linux is also used in small embedded devices and industrial control systems. Linux end-user distributions are also becoming attractive as desktop environments.
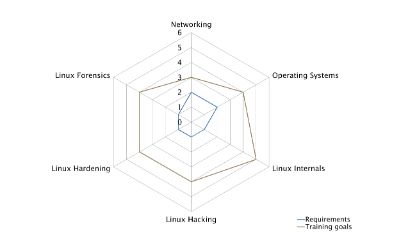
The network connectivity of Linux systems exposes them to hostile and malicious cyber attacks. The CAS Linux Cyber Security teaches students the internals of Linux, how to harden Linux systems, and various types of hacking attacks targeting Linux servers. The CAS Linux Cyber Security completes with a module on Linux forensics in the event of compromise or abuse.
Education goals
This continuing education program has practical learning objectives. Students completing the CAS Linux Cyber Security will have deep understanding of how Linux works and how Linux can be hacked. Students will have the skills to securely harden Linux systems and perform digital forensics in the event of an incident.